October 2nd, 2025 | by Dawid Marniok
A Technical Leader's Guide to Infrastructure Integration and Transformation
Table of contents
Introduction: A Tale of Two Worlds
In today’s dynamic business environment, mergers and acquisitions are becoming increasingly common. Companies merge for various reasons: to increase market share, acquire new technologies, enter new markets, or gain skilled teams. Regardless of the motivation, every organization going through such transformation faces similar technical challenges.
Imagine this scenario: it’s just been announced that your company is acquiring another organization. The board’s first reaction? “We need to integrate the systems and infrastructure as quickly as possible.” Sounds simple, right? Well… not quite.
Below is a visual contrast between two typical cloud environments — the first dominated by AWS microservices, the second by Azure’s event-driven architecture
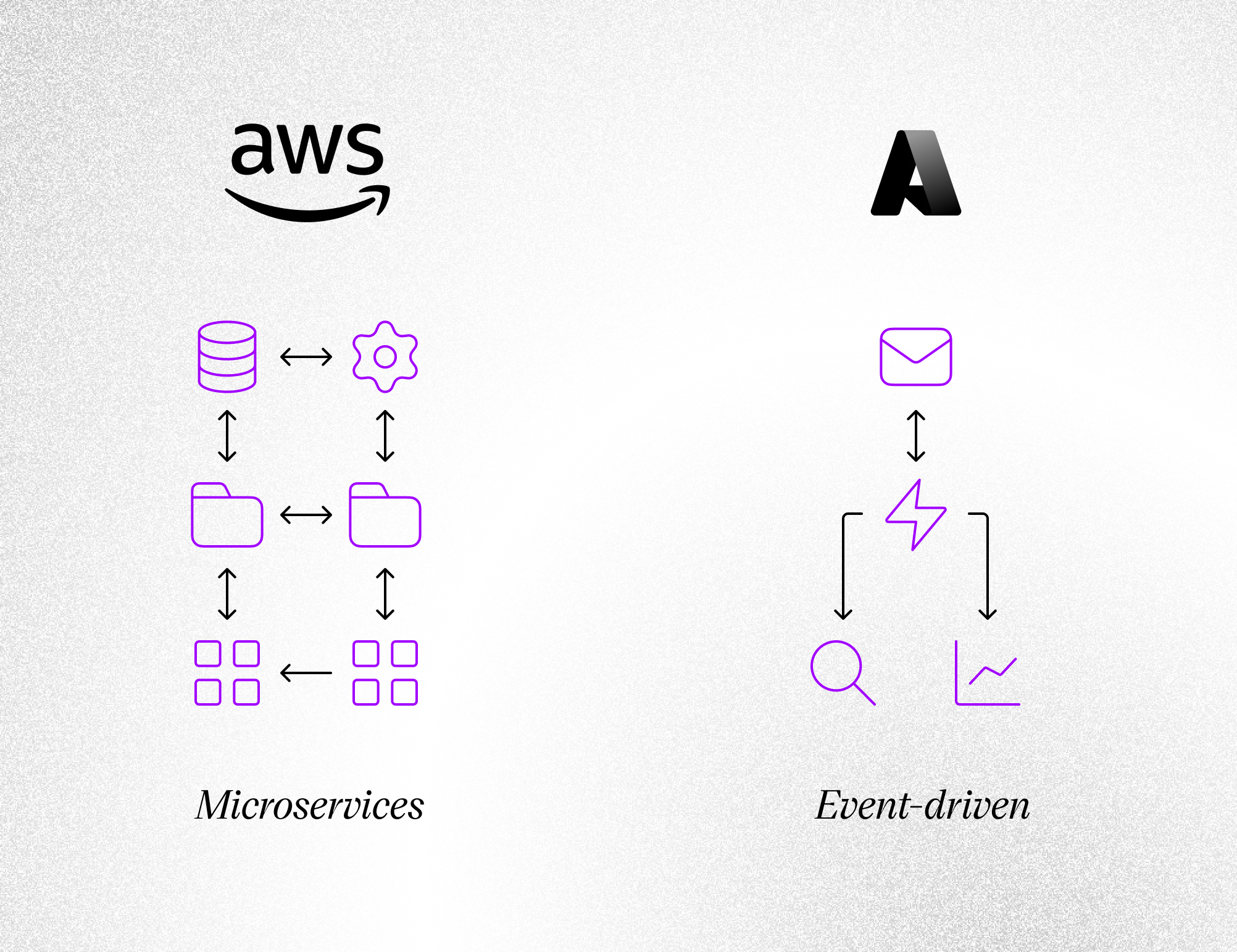
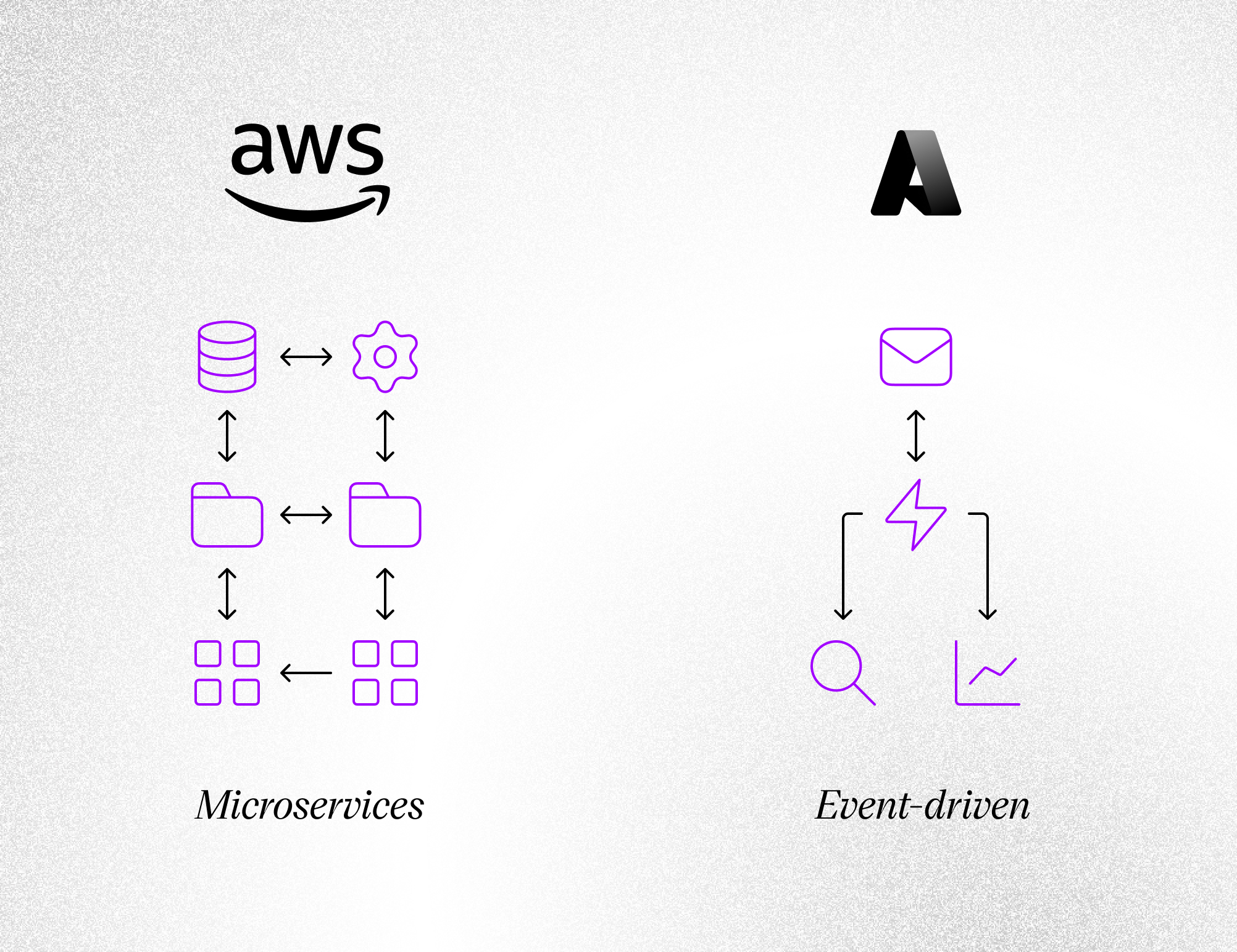
Reality Check
In an ideal world, post-merger consolidation would be a smooth transition of all systems into one cohesive environment. Reality, however, is far more complicated.
Let’s look at a typical scenario:
Company A: Mature organization, 100% on AWS
200+ microservices
Deep integration with AWS services
Years of automation investment
Team of AWS experts
200+ microservices
Deep integration with AWS services
Years of automation investment
Team of AWS experts
200+ microservices
Deep integration with AWS services
Years of automation investment
Team of AWS experts
200+ microservices
Deep integration with AWS services
Years of automation investment
Team of AWS experts
200+ microservices
Deep integration with AWS services
Years of automation investment
Team of AWS experts
Company B: Innovative scale-up on Azure
Modern event-driven architecture
Heavy use of Azure-native services
Rapid development pace
Team of cloud-native developers
Modern event-driven architecture
Heavy use of Azure-native services
Rapid development pace
Team of cloud-native developers
Modern event-driven architecture
Heavy use of Azure-native services
Rapid development pace
Team of cloud-native developers
Modern event-driven architecture
Heavy use of Azure-native services
Rapid development pace
Team of cloud-native developers
Modern event-driven architecture
Heavy use of Azure-native services
Rapid development pace
Team of cloud-native developers
First Questions from the Board
- When can we move everything to one cloud?
- How much will we save through consolidation?
- How quickly can the teams start collaborating?
These questions seem logical, but each opens up a whole series of complex technical, organizational, and business challenges
Technical Challenges
Architectural Challenges
Differences in Architectural Approach
The problem of architectural differences isn’t just about technical preferences. It’s about fundamental differences in how systems and their evolution are conceptualized. Each organization develops its own approach to architecture over years, deeply rooted in its technical culture, processes, and operating methods.
These differences often result from organizational evolution, history, specific business requirements, and team experiences. For example, a fintech company might have opted for an event-driven architecture due to the need to handle a large number of real-time transactions. Meanwhile, a traditional financial institution might have evolved around stable, monolithic systems that proved effective in handling complex business processes.
Cloud-Native Services and Vendor Lock-in
What about vendor lock-in? This isn’t just a theoretical problem from PowerPoint presentations anymore. It’s a real challenge that can significantly impact the costs and timeline of the entire consolidation process. Imagine one company built their entire infrastructure around AWS Lambda and DynamoDB, while the other is deeply integrated with Azure Functions and CosmosDB. There’s no simple “lift and shift” here – every change requires deep architectural consideration.
The table below compares key services across AWS and Azure, highlighting potential incompatibilities during migration or integration.


Example incompatibilities we must deal with:
AWS Lambda vs Azure Functions
Amazon SQS vs Azure Service Bus
DynamoDB vs Cosmos DB
CloudWatch vs Azure Monitor
AWS Lambda vs Azure Functions
Amazon SQS vs Azure Service Bus
DynamoDB vs Cosmos DB
CloudWatch vs Azure Monitor
AWS Lambda vs Azure Functions
Amazon SQS vs Azure Service Bus
DynamoDB vs Cosmos DB
CloudWatch vs Azure Monitor
AWS Lambda vs Azure Functions
Amazon SQS vs Azure Service Bus
DynamoDB vs Cosmos DB
CloudWatch vs Azure Monitor
AWS Lambda vs Azure Functions
Amazon SQS vs Azure Service Bus
DynamoDB vs Cosmos DB
CloudWatch vs Azure Monitor
Storage and Data: Where’s the Truth?
The data layer is often the biggest headache. While applications can be rewritten or adapted, data… well, that’s a different story entirely. Take a simple example: one company uses DynamoDB with its specific data consistency model, while the other relies on CosmosDB with a completely different approach to partitioning and replication.
What does this mean in practice?
Different data consistency models
Distinct APIs and access patterns
Incompatible partitioning mechanism
Vendor-specific optimizations
Different data consistency models
Distinct APIs and access patterns
Incompatible partitioning mechanism
Vendor-specific optimizations
Different data consistency models
Distinct APIs and access patterns
Incompatible partitioning mechanism
Vendor-specific optimizations
Different data consistency models
Distinct APIs and access patterns
Incompatible partitioning mechanism
Vendor-specific optimizations
Different data consistency models
Distinct APIs and access patterns
Incompatible partitioning mechanism
Vendor-specific optimizations
Operational Dilemmas: Who’s Keeping Watch?
Monitoring: Seeing Everything, But How?
Imagine you’re a DevOps engineer on night duty. Suddenly you get an alert… but from which system? CloudWatch or Azure Monitor? Or both? How do you correlate these events? These aren’t theoretical questions – they’re real challenges teams face every day.
Main challenges:
Different metric and log formats
Incompatible APIs and integrations
Lack of unified view
Complexity in event correlation
Different metric and log formats
Incompatible APIs and integrations
Lack of unified view
Complexity in event correlation
Different metric and log formats
Incompatible APIs and integrations
Lack of unified view
Complexity in event correlation
Different metric and log formats
Incompatible APIs and integrations
Lack of unified view
Complexity in event correlation
Different metric and log formats
Incompatible APIs and integrations
Lack of unified view
Complexity in event correlation
The following diagram illustrates how alert confusion can arise in a multi-cloud setup, making incident response more complex and fragmented.
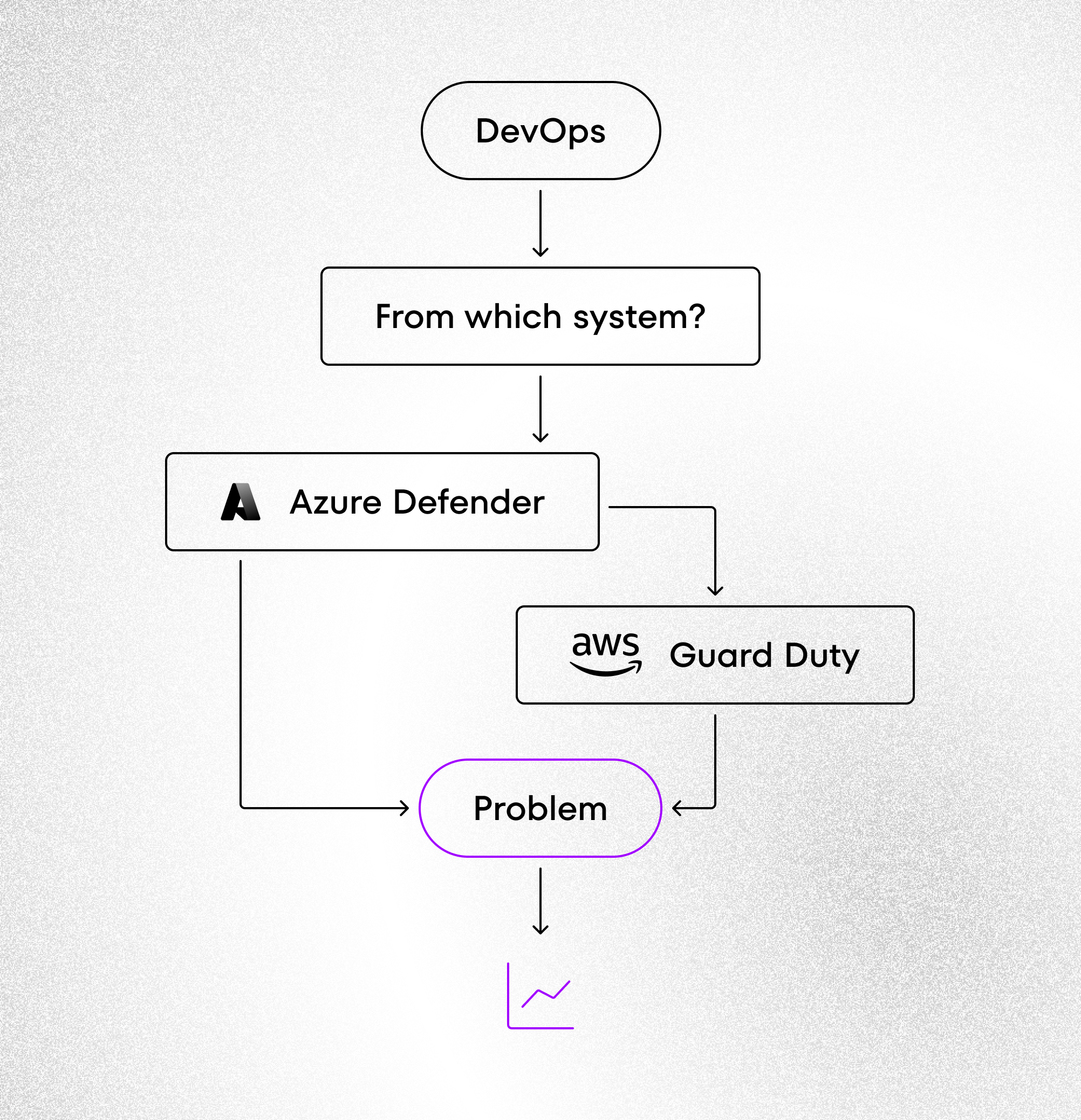
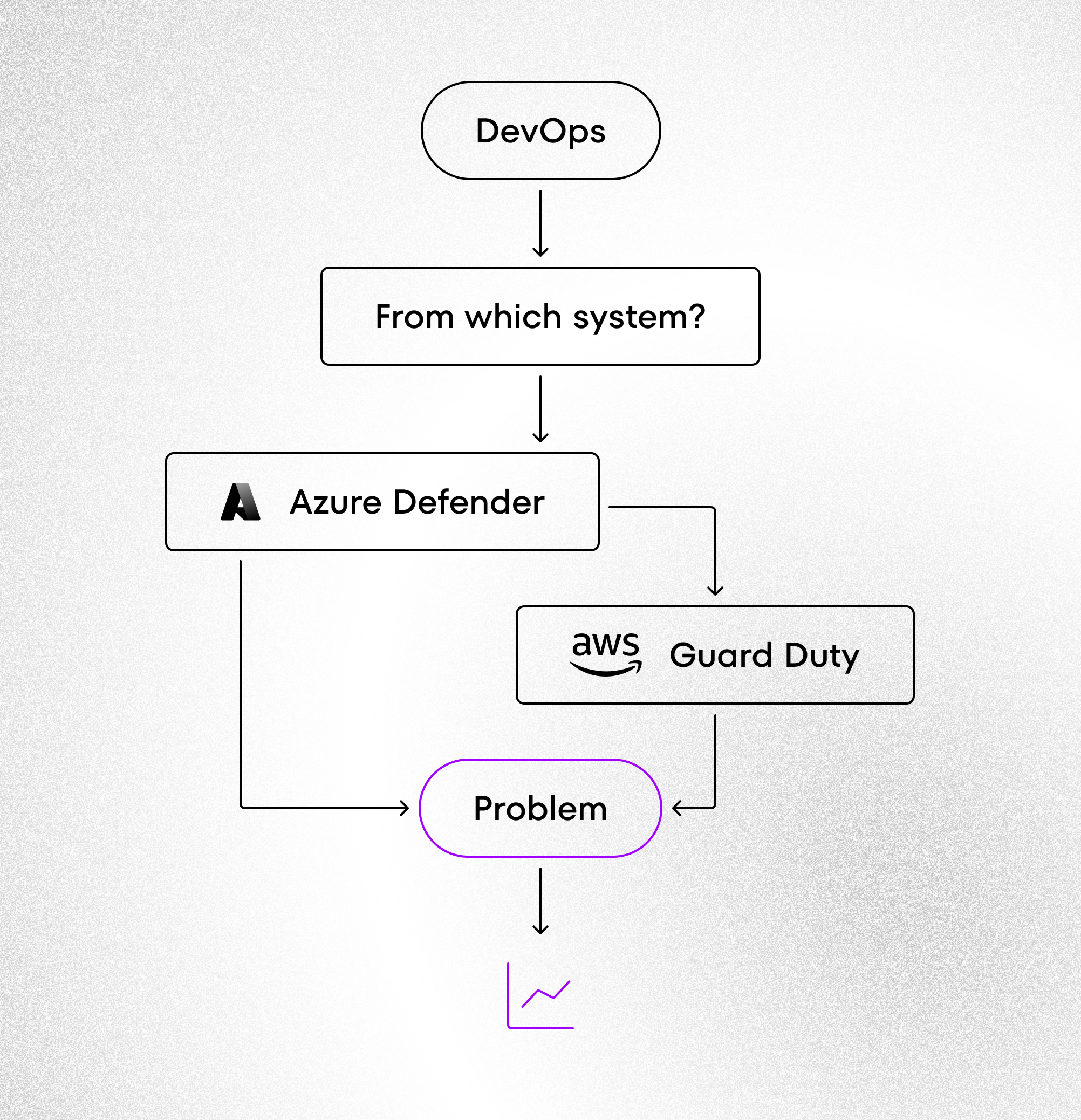
Incident Management: Who Responds and How?
And what happens when something goes wrong? Who should respond? The AWS team or the Azure team? Or both? How do you ensure quick reaction in an environment where every minute of downtime could cost thousands?
Key aspects:
- Different detection systems (AWS GuardDuty vs Azure Defender)
- Distinct response procedures
- Platform-specific remediation steps
- Complex escalation procedures
Security and Compliance: Double Standards?
Identity Management: Who Has Access to What?
Identity management in a multi-cloud environment isn’t just a technical challenge – it’s also a security and compliance issue. How do you ensure the right people have the right access to the right resources, regardless of platform?
Key questions:
- How to integrate Azure AD with AWS IAM?
- How to ensure consistent SSO?
- How to audit access in a distributed environment?
- How to manage cross-cloud permissions?
Action Plan: Where to Start?
When facing the complexity of multi-cloud integration in post-merger scenarios, it’s crucial to approach the challenge with a well-thought-out strategy. Rather than attempting to solve all problems simultaneously, which often leads to chaos and burnout, it’s better to break down the process into manageable phases.
Here’s a visual summary of the proposed three-phase integration plan. Each step builds on the previous, balancing risk and business value.
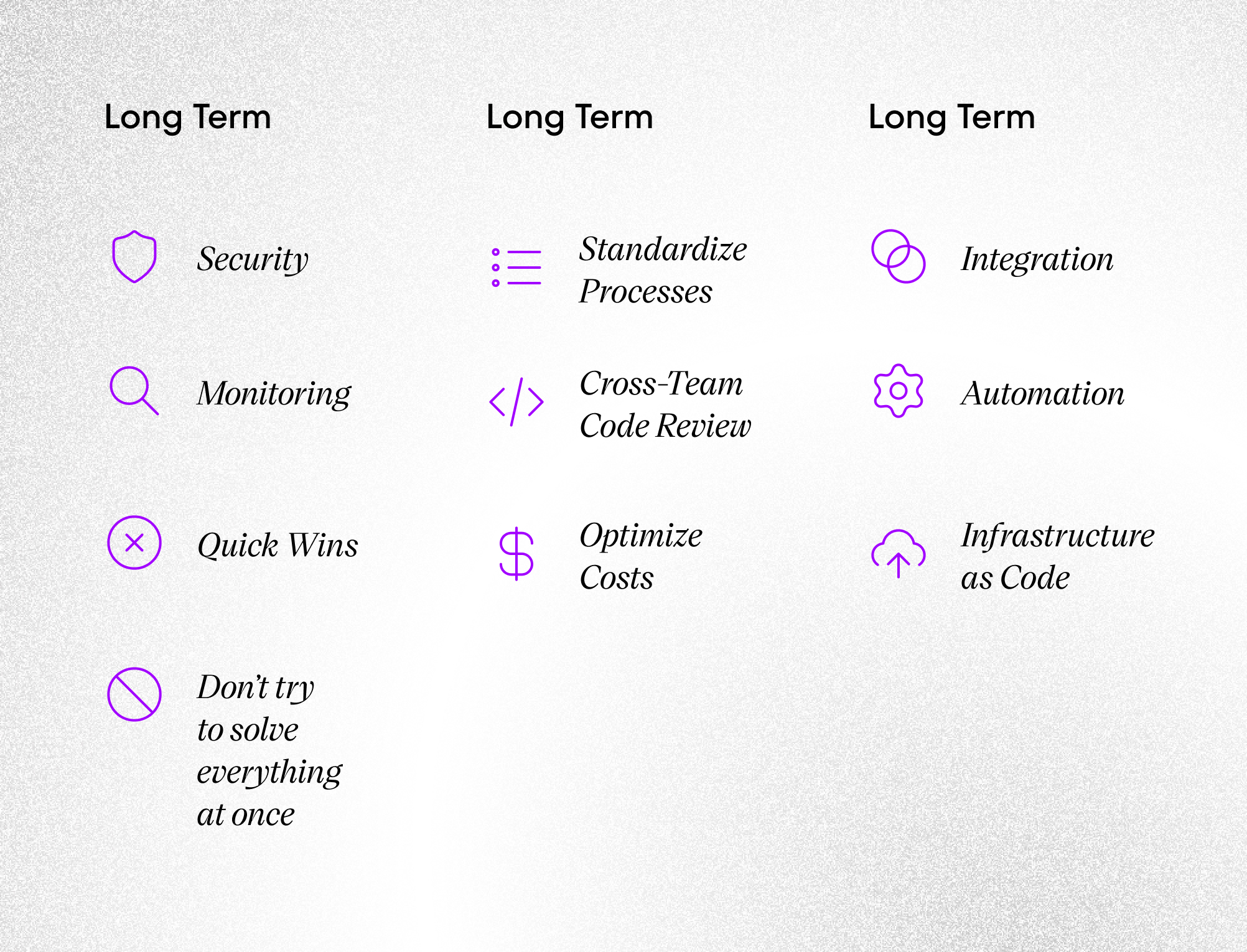
Think of it as building a house – you need solid foundations before you can start working on the walls and roof. The same principle applies here: start with the essential elements that will support future integration efforts, then gradually build up more complex solutions. This approach not only reduces risk but also allows teams to adapt and learn from early experiences.
Let’s break down this journey into three distinct phases, each with its own set of priorities and objectives:
Short Term: Foundations
- Ensure basic security
- Unify identity management
- Establish basic access policies
- Implement security monitoring
- Establish baseline monitoring
- Implement cross-cloud alerting
- Configure basic dashboards
- Define critical metrics
- Identify quick wins
- Find areas of least resistance
- Focus on critical business integrations
- Don’t try to solve everything at once
Medium Term: Stabilization
- Standardize processes
- Unify operational procedures
- Define common DevOps practices
- Introduce cross-team code review
- Optimize costs
- Identify duplicate services
- Assess consolidation opportunities
- Implement cross-cloud cost monitoring
Long Term: Optimization
- Full integration (where it makes sense)
- Consolidate similar systems
- Standardize architecture
- Implement common development practices
- Automation
- Build cross-cloud CI/CD
- Automate environment management
- Implement Infrastructure as Code
Summary: A Realistic Approach
Post-M&A consolidation in a multi-cloud environment is a marathon, not a sprint. Like any marathon, it requires careful preparation, proper pacing, and a clear understanding of the finish line. Success in this journey isn’t about speed – it’s about making sustainable, business-aligned decisions that create long-term value.
The keys to success are:
- Realistic situation assessment
- Understanding both technical landscapes in depth
- Acknowledging existing constraints and limitations
- Identifying true integration priorities versus “nice-to-haves”
- Pragmatic approach to integration
- Starting with high-impact, low-risk initiatives
- Building integration patterns that can be reused
- Maintaining operational stability throughout the process
- Focus on business value
- Aligning technical decisions with business objectives
- Quantifying the ROI of each integration initiative
- Prioritizing changes that directly impact business outcomes
- Patience and methodical action
- Taking time to build proper foundations
- Learning from early integration experiences
- Adjusting the approach based on feedback and results
It’s crucial to remember that not every system needs to be migrated or transformed. The “lift and shift” mentality rarely serves well in complex multi-cloud scenarios. Sometimes, maintaining the status quo with an appropriate level of integration is not just acceptable – it’s the best solution. This might mean keeping certain systems in their original cloud while ensuring they can effectively communicate with other components.
The most important thing is finding the right balance between technical ambitions and business needs. This balance will be different for each organization, depending on factors like:
Business priorities and timeline
Available resources and expertise
Regulatory requirements
Cost constraints
Risk tolerance
Business priorities and timeline
Available resources and expertise
Regulatory requirements
Cost constraints
Risk tolerance
Business priorities and timeline
Available resources and expertise
Regulatory requirements
Cost constraints
Risk tolerance
Business priorities and timeline
Available resources and expertise
Regulatory requirements
Cost constraints
Risk tolerance
Business priorities and timeline
Available resources and expertise
Regulatory requirements
Cost constraints
Risk tolerance
Success in multi-cloud integration isn’t about achieving perfect technical harmony – it’s about creating a practical, sustainable environment that supports business growth and innovation while managing risk and complexity effectively.